![No Junk Mail]()
It’s happened to everyone at one point or another. You get an email, you open it, maybe you click on something, and later you think “Wait…what was that
really?” With phishing attempts and spam email becoming more sophisticated every day, they’re getting better at tricking people. Even the smartest person can easily make a mistake and click on something they shouldn’t. So rest assured, you’re not an idiot if you fall prey to a phishing attempt – here’s why.
Spam email and links look better than ever, they’re more personalized than they used to be, and they can even include information that makes it seem like they really do know their target. Now, instead of “Dear Sir/Madam” I’m seeing “Danielle,” and instead of obvious false links, they often look legitimate unless scrutinized – which not everyone who doesn’t work in IT does every time they get an email. (I don’t blame you if you don’t! If I didn’t work where I do, I probably wouldn’t either.) Even working in IT, I don’t always have time to analyze an email to the extent that I know is necessary.
Everyone is busy, and the attackers know it. Bad guys prey on the increased sense of urgency we all face at work, and they’re hoping to override our logic with emotions. Their goal is to scare us, trick us, and most of all make it second nature to complete whatever action they will benefit from. Whether that’s clicking a link, transferring money, or opening an attachment, they’re going to try every tactic they can to make that happen.
A few things in particular are prevalent right now. Spear phishing, O365 email scams, CEO fraud, and the ever popular bad attachment are what we see most often.
Spear Phishing
This specific type of phishing attack is gaining in popularity because its highly customized approach often yields better results than generic phishing attempts. By combing through a combination of easily accessible information (such as your social media profiles, company bios, published articles and more), an attacker can find out who you work with, what your job function is and how to more effectively target you with personalized content. For more on spear phishing, check out
this blog.
Tip: Avoid Spear Phishing attacks by closely examining the subject, contents and sender information of the email. Look for letters switched for numbers and vice versa, poor grammar and vague information. Hover over links and compare the text to the URL. Limit the information about work posted to social media when possible.
O365 Phishing
O365 email scams are another heavy hitter, because so many people are using the platform now and as Tim Weber said in his blog,
“It’s Where the Money Is”. With so many organizations on O365, it’s fairly easy to send out emails warning users of “quarantined emails” needing release, account lockouts and more. Here’s an example of one I got:
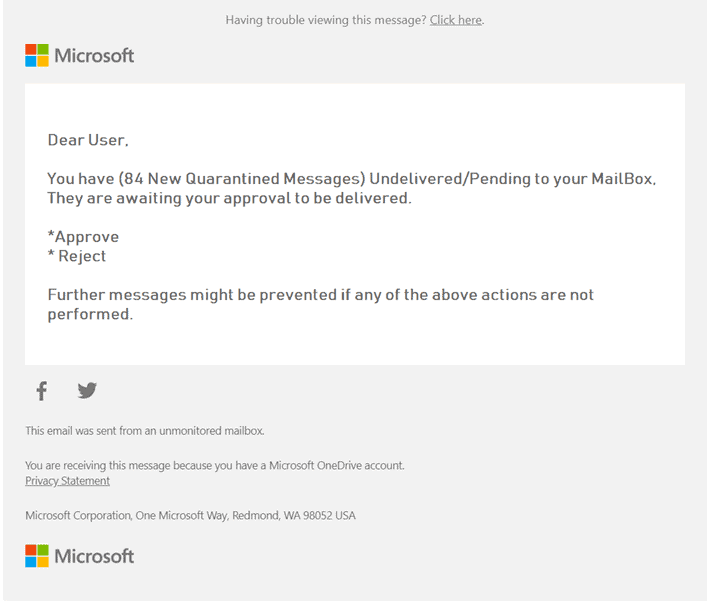
I don’t know about you, but my Delve analytics (thanks Microsoft!) tell me I open 75% of emails within half an hour of receiving them. If everyone is doing that, chances are they’re looking quickly and are less likely to catch those small tells that an email might not be what it looks like at first glance. Sure, the subject line is off, as are the To: and From: fields, but you might not catch that if you’re taking a quick peek, especially on a mobile device. Learn more about the O365 scams we’re seeing
here.
Tip: Protect yourself from O365 scams by closely examining emails you get prior to opening any attachments or clicking on any links. Look for grammatical errors or cases where things are close, but not quite right. (Example: MICROSOFT vs MICR0S0FT) If you have any doubts, go to your IT team or provider directly.
CEO Fraud
CEO Fraud was at its peak in 2016, and it hasn’t slowed down much. Spam emails impersonating a CEO or high ranking person at a company, asking another employee to do something such as transfer funds or pay an invoice (which is fake) are still circulating. The hackers don’t slouch on their research either, and they often use details they can find on social media to use these strategies when people are traveling and might plausibly ask someone at the office to do something for them. The
FBI has been involved with many of these cases, due to the high stakes and financial losses involved.
Tip: If you get a suspicious request from someone, take it out of email to verify it. Call them, text them, go to their office – before completing the request.
Malicious Attachments
Last but not least, the bad attachment. From Google Docs to Word, bad attachments can come in many shapes and sizes, and often just opening them is enough to compromise the security of your device, and maybe even your network. Popular ones are invoices, resumes and things like shipping labels – types of documents that would be perfectly normal to receive from legitimate sources.
Tip: Be cautious of the sender and the context. Does it make sense for you to have received it? Does that person have any reason to be sending it to you? Is it a document you would normally be consulted on? These things, coupled with suspicious signatures and file names can indicate that the attachment may not be legitimate.
What do I do if I get a Phishing Email?
The bottom line is, you’re going to receive a spam email at some point. Probably more than one. The most important thing is that if you open it, click it, download it – whatever – that you tell someone. Whether it’s your IT provider, or the person responsible for IT in your organization, you need to let someone know of the spam email so that they can minimize any dwell time (the time when a ‘bad guy’ is in your system) and limit the possible damage. Don’t be embarrassed, don’t worry about getting in trouble.
The best thing you can do to learn from a spam email incident and ensure there’s less impact is to get ahead of the situation by quickly letting someone on your security team know. If you’re more likely to be the person someone is reporting this event to, the best thing you can say in response is “thank you so much for telling me.” Encouraging people to come forward instead of hiding their mistake will not only make them feel better, it will make your organization safer by helping to build a culture of security-minded employees.
If you need more information on ways to keep your organization secure, visit the blogs linked to in this article. There are tips for staying safe and spotting fake emails in many of them, as well as more information on why attackers do what they do.
Security Awareness Training is a great way to educate your whole team on the current threats and how to avoid them. We’re happy to come to your location and deliver the training to your team in person.
Download our free Cybersecurity Checklist: 14 Ways to Protect Your Business from a Cyber Attack
81% of all breaches happen to small and medium-sized businesses.
97% of these security breaches could have been prevented. Protect your business against today’s top cybersecurity threats with tips from our Cybersecurity Checklist –
download it here today.
 It’s happened to everyone at one point or another. You get an email, you open it, maybe you click on something, and later you think “Wait…what was that really?” With phishing attempts and spam email becoming more sophisticated every day, they’re getting better at tricking people. Even the smartest person can easily make a mistake and click on something they shouldn’t. So rest assured, you’re not an idiot if you fall prey to a phishing attempt – here’s why.
Spam email and links look better than ever, they’re more personalized than they used to be, and they can even include information that makes it seem like they really do know their target. Now, instead of “Dear Sir/Madam” I’m seeing “Danielle,” and instead of obvious false links, they often look legitimate unless scrutinized – which not everyone who doesn’t work in IT does every time they get an email. (I don’t blame you if you don’t! If I didn’t work where I do, I probably wouldn’t either.) Even working in IT, I don’t always have time to analyze an email to the extent that I know is necessary.
Everyone is busy, and the attackers know it. Bad guys prey on the increased sense of urgency we all face at work, and they’re hoping to override our logic with emotions. Their goal is to scare us, trick us, and most of all make it second nature to complete whatever action they will benefit from. Whether that’s clicking a link, transferring money, or opening an attachment, they’re going to try every tactic they can to make that happen.
A few things in particular are prevalent right now. Spear phishing, O365 email scams, CEO fraud, and the ever popular bad attachment are what we see most often.
It’s happened to everyone at one point or another. You get an email, you open it, maybe you click on something, and later you think “Wait…what was that really?” With phishing attempts and spam email becoming more sophisticated every day, they’re getting better at tricking people. Even the smartest person can easily make a mistake and click on something they shouldn’t. So rest assured, you’re not an idiot if you fall prey to a phishing attempt – here’s why.
Spam email and links look better than ever, they’re more personalized than they used to be, and they can even include information that makes it seem like they really do know their target. Now, instead of “Dear Sir/Madam” I’m seeing “Danielle,” and instead of obvious false links, they often look legitimate unless scrutinized – which not everyone who doesn’t work in IT does every time they get an email. (I don’t blame you if you don’t! If I didn’t work where I do, I probably wouldn’t either.) Even working in IT, I don’t always have time to analyze an email to the extent that I know is necessary.
Everyone is busy, and the attackers know it. Bad guys prey on the increased sense of urgency we all face at work, and they’re hoping to override our logic with emotions. Their goal is to scare us, trick us, and most of all make it second nature to complete whatever action they will benefit from. Whether that’s clicking a link, transferring money, or opening an attachment, they’re going to try every tactic they can to make that happen.
A few things in particular are prevalent right now. Spear phishing, O365 email scams, CEO fraud, and the ever popular bad attachment are what we see most often.
 I don’t know about you, but my Delve analytics (thanks Microsoft!) tell me I open 75% of emails within half an hour of receiving them. If everyone is doing that, chances are they’re looking quickly and are less likely to catch those small tells that an email might not be what it looks like at first glance. Sure, the subject line is off, as are the To: and From: fields, but you might not catch that if you’re taking a quick peek, especially on a mobile device. Learn more about the O365 scams we’re seeing here.
I don’t know about you, but my Delve analytics (thanks Microsoft!) tell me I open 75% of emails within half an hour of receiving them. If everyone is doing that, chances are they’re looking quickly and are less likely to catch those small tells that an email might not be what it looks like at first glance. Sure, the subject line is off, as are the To: and From: fields, but you might not catch that if you’re taking a quick peek, especially on a mobile device. Learn more about the O365 scams we’re seeing here.
