
We’re constantly on the lookout for the latest email and phishing scams, and there’s one we have seen going around today revolving around Microsoft O365. In our previous blog, Why Are Attackers Targeting O365? It’s Where the “Money” Is, we mentioned that with the sheer number of people moving to the cloud, it’s an extremely target rich environment. Malicious emails are a numbers game – and the more people you can send them to, the more people you’re likely to get to click on the bad link.
Real Examples of O365 Phishing Emails
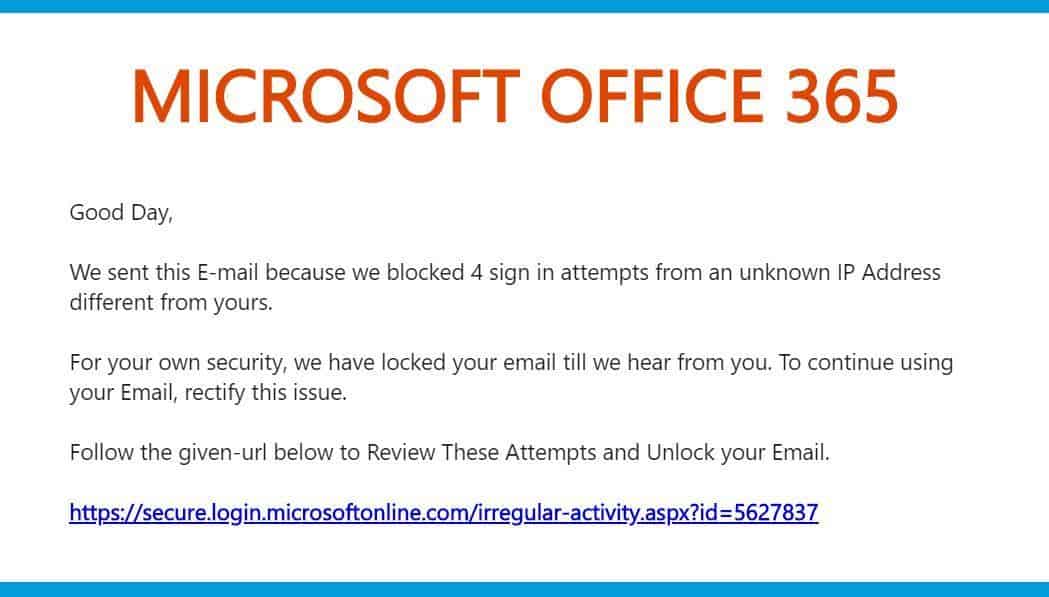
Even when you’re careful, it can be easy to overlook certain things – especially during the workday when you’re rushing to get through your emails, or something is deliberately crafted to inspire panic, like the message below. Examining the entire email, there are subtle errors throughout, but it has definitely come a long way from the “Dear Sir/Madam” phishing emails of the past. The attacker in this message wrote it to prey on the fact that when confronted with a possible security issue, people are immediately concerned and will try to fix it. Not only are they saying someone is trying to sign into your account – they’re saying they have tried multiple times!
This is meant to inspire you to quickly open the email and click the link – which looks fairly legitimate, including keywords you’ll find familiar like “secure,” “login,” and “Microsoft online”. If you do have O365, that link might look right to you at first glance. But if you hover over it, you’ll see it’s not going where it says it will. They also used colors consistent with some Microsoft branding, but looking closely you can see the email has several grammatical and spelling errors, and is not written in a way consistent with how a company like Microsoft communicates. There’s a Hotmail address displaying as the sender, and an official Microsoft email certainly wouldn’t be coming from there.
As a reminder – Microsoft will not reach out to you by email or phone. The only time that may happen is if you have a legitimate support issue and YOU reach out to THEM. They will not initiate contact in this way.
10 Tips to Stay Safe
Here are ten tips from one of our TAC experts, Stefanie Fontana, on what you should be looking for to keep yourself safe.
- Reputable organizations will never ask for sensitive information via email or text message.
- Check the sender’s email address – not just the display name. Any name can be entered to give the illusion it’s from a legitimate person.
- Be wary of emails with generic salutations such as “valued customer,” etc.
- Look carefully for I’s, L’s, 1’s, O’s, 0’s…these can all be used to make an email address look legitimate while actually being misspelled.
- Look for any spelling mistakes or grammatical errors.
- Keep your computers and applications updated at all times, or use a Managed Service to have them patched regularly as updates to address vulnerabilities are released.
- Type out the web address in the browser yourself versus clicking on links to navigate to a site.
- Hover over any links to see where they actually point to. Anything can be put into the display text for a link, regardless of what the URL actually is.
- Think about whether or not the sender actually has a legitimate reason to contact you. If you don’t know them, their company, or their email address, don’t feel guilty not opening it!
- Above all, trust your instincts. If something looks off, or is different from anything you have gotten from a company or sender before – it might not be as legitimate as it seems.
If you do click on something, let us know and we’re always happy to help. Don’t ever feel bad reporting it! If you click on a suspicious link and it opens your systems to attack, it’s always easier to control the damage early on rather than waiting for someone to find out where the attacker got in (which trust me, they will eventually!). If you think your team needs help determining what they should be suspicious of, reach out to us to schedule a Security Awareness Training.
